Metasploitable is a virtual machine image that is intentionally vulnerable and created for cybersecurity students to learn ethical hacking on own environment.
Metasploitable2 is a second version of Metasploitable and it is very good and safe to use and learn penetration testing. Attacking others system with out proper permission will be illegal, and they won't give permission to hack their system to new learners.
So, we need to set up own vulnerable system in our penetration testing lab and learn thing by own. Previously we talked about setting up some easy penetration testing lab setup. Now we learn how we can install Metasploitable2 in our Kali Linux system. We can find a lots of tutorial on the internet but they all install it on Windows Virtualbox/VMware.Metasploitable2 is a OS disk image file that can be run from VMware/VirtualBox. So first we need to have a virtualization software like VMware or VirtualBox. Lets install KVM (Kernel Virtual Machine) in our Kali Linux system by using following command:
Now this will take some time so, we are going for a coffee 🍵. This also requires a reboot to finish the installation. If this installation process got any error for dependencies then we need to install dependencies manually or our comment box is opened for solutions.
After installing this we can run KVM by using following command:
After running this command our virtual machine manager box will opened as the following screenshot:
 |
| KVM main menu |
It is a quite big image file with 865MB in size. Downloading this depends on internet speed. After download we can extract the zip file as we did it in the following screenshot:
 |
| Our required file is highlited |
Now we click on forward option, and we got a window like following:
Here we need to click on Browse>Browse Local ,then we select our Metasploitable2 disk image. Shown in the next screenshot:Then we click on Open. Then our image file will selected and in the operating system we search for Generic(default) to set it. Shows in the following screenshot:Now we move forward and KVM will ask us for RAM and CPU. The Default will be 1024 MB(1GB) RAM and 1 CPU. We will go with the default. Metasploitable2 can be run easily on 512 MB RAM.
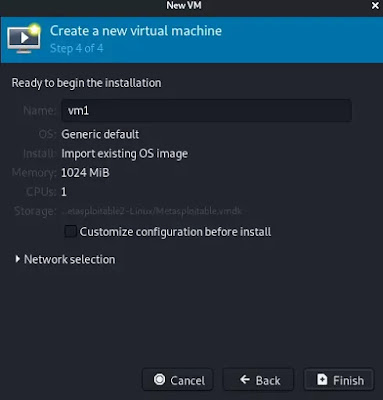
Here we can give any name to our machine and click on "Finish".
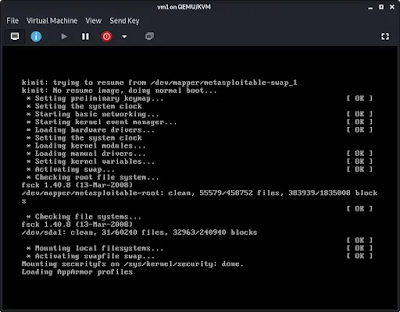
YOO, our Metasploitable2 system will start on KVM and run all the services inside it. As we can see in the following screenshot:
After finishing the set up in some seconds it will ask for login. The default username and password will be msfadmin . After a sucessful login we can see the command line interface of metasploitable as following screenshot:
Now we check the IP address of the Metasploitable2 machine by using following command:
The output on the metasploitable machine is following:
Now in the above screenshot we can see that our Metasploitable2 machine's Ip address is 192.168.122.118. This may be diffrent for everyone becase our local network assign this IP address.
We can open this IP address on our browser.
Now we can practice our penetration testing skills on this machine. We can find vulnerabilities on this machine and exploit it.
For an example we just did a nmap scan to find open ports, and we found a lots of vulnerable ports.
We just need to find the way to exploit these vulnerabilities. We can use msfconsole or Google to find and exploit them
















Comments