Information is power. If we have clear knowledge about someone then we can easily win him. Gmail or Google Mail is the most popular mail service in the world almost every person have a Google account or Gmail id. Now we can know a lots of information of anyone from their mail address.
To collect someone's account information we use GHunt tool. GHunt is an OSINT tool written in Python3 to extract information from any Google Account using an email on our Kali Linux system. This tool will be very useful to gather information on target user. Then the attack can use these valuable information against the target.
GHunt can collect following information about a person
- Owner's name.
- Last time the profile was edited.
- Google ID.
- If the account is a Hangouts Bot.
- Activated Google services (YouTube, Photos, Maps, News360, Hangouts, etc.)
- Possible YouTube channel.
- Possible other usernames.
- Public photos (P).
- Phones models (P).
- Phones firmwares (P).
- Installed softwares (P).
- Google Maps reviews (M).
- Possible physical location (M).
Now the (P) marked features requires the target account to have the default setting of Allow the people you share content with to download your photos and videos on the Google AlbumArchive, or if the target has ever used Picasa linked to their Google account.
Those features marked with a (M) require the Google Maps reviews of the target to be public (they are by default).
Installation of GHunt in Kali Linux
To install GHunt in our system we need to clone it from it's GitHub repository by sing following command:
The following screenshot shows the output of preceding command:
Now we need to navigate to the GHunt directory by using cd command:
Here before run the tool we need to install some requirements on our system to run this tool. To do that we use following command:
The following screenshot shows installing the requirements process.
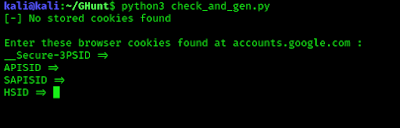
First we need to generate cookies 🍪 and tokens from our exiting Google Account. For that we use following command:
Here we need 4 required cookies. If they are valid, GHunt will generate the Authentication token and the Google Docs & Hangouts tokens.
Generating Cookies for GHunt
Here we suggest to use an empty or new Google Account. We shouldn't give this tool our primary Google Account's information/cookies.
- On our new/empty Google Account we need to go to the link https://accounts.google.com then login here if we are not already logged in.
- After that, open the Dev Tools window and navigate to the Storage tab (Shift + F9 on Firefox) (It's called "Application" on Chrome). If we don't know how to open it, we just right-click anywhere and click on the "Inspect Element".
- Then we'll find every cookie that we need, including the 4 ones.
Then we need to paste our required cookies on GHunt tool. The cookies are
- __Secure-3PSID
- APISID
- SAPISID
- HSID
GHunt Against Google Accounts
Now we can run this tool. We run this tool against our own mail id for an example. We are hiding some personal details. We run GHunt by following command:
Then it will show the name and other sensitive information regarding the mail id.
How to be Safe
We can keep safe collection of metadata from our Google Photos account.
Given that Google shows "X require access" on our Google Account Dashboard, we might imagine that we had to explicitly authorize another account in order for it to access our pictures; but this is not the case. Any account can access our AlbumArchive (by default):
Here's how to check and fix the fact that we're vulnerable (which we most likely are).
Now we need to go to https://get.google.com/albumarchive/ while logged in with our Google account. We will be automatically redirected to our correct albumarchive URL (https://get.google.com/albumarchive/OUR-GOOGLE-ID-HERE). After that, we click the three dots on the top left corner, and click on setting.
Then, we just need to un-check the only option there.












Comments